The Metaspike CTF has started! Lately I haven’t had a lot of time for CTFs, but this one is focusing on email forensics. Since it something I’ve taken an interest in recently I thought I’d give it a shot.
If you'd like to play along, the challenge has been archived here
Content
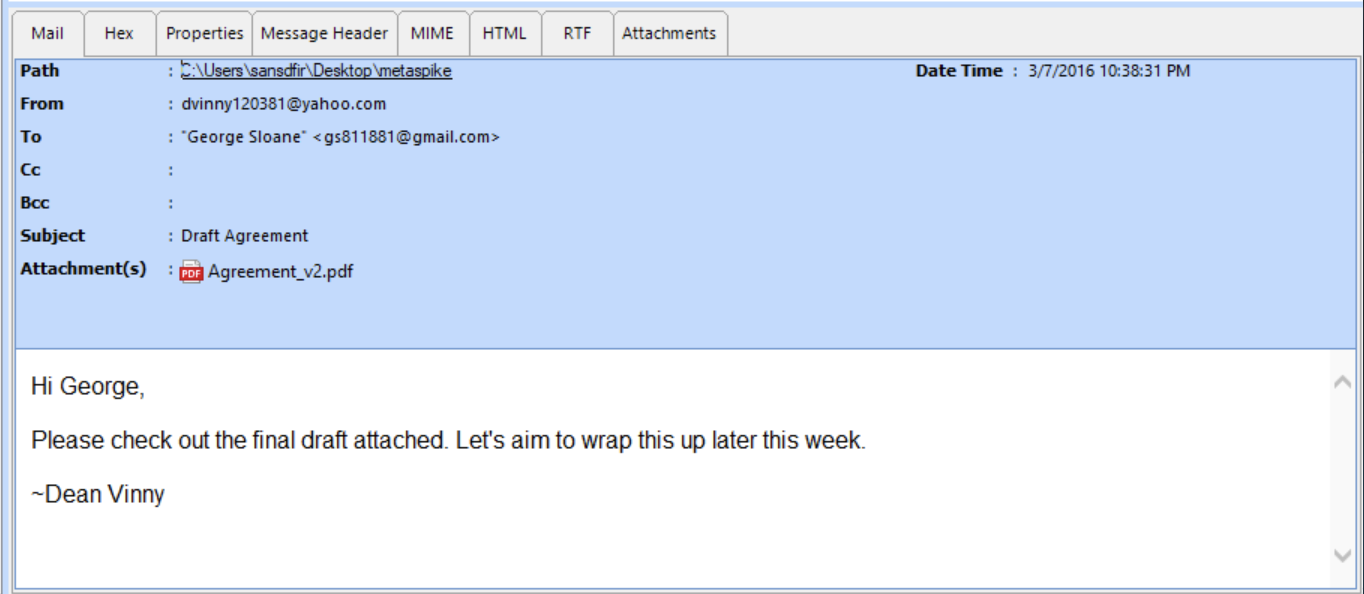
We were provided with an email, in EML format, that is shown here with Systools EML Viewer. On the face of it it’s a simple email, dated March 7 2016 between a Yahoo and Gmail address with a PDF attachment.
Header
The EML viewer has a couple methods of viewing the email header; either in text format under “Message Header” or parsed into fields under “Properties”. But, because the email is in EML format, we can view it in any text editor.
Below the email is displayed in VSCode with some email header highlighting.

Other tools I’ve found useful for email:
They’ve all proven quite useful for slightly different reasons – between them allowing for visualisation, CTI lookups, and dumping the data out into JSON!
Initial observations
On the face of it, there’s a lot of great information held in this header. We can see X-Headers, authentication headers (ARC, DKIM, SPF), and the standard received headers.
We can also see a lot of different timestamps that may prove useful later on.
Question 1
The first question was a seemingly simple one. Is this email fraudulent or legit!?

There are a couple different ways to tackle this question – bearing in mind the email provided to us is basically just a text file, so everything can be edited.
Thankfully there are a lot of timestamps (which may or may not be correct), there’s a DKIM signature, and, the thing I used to answer the question, an X-Mailer.
The email is purportedly from 2016, but the X-Mailer shows: “X-Mailer: WebService/1.1.17111 YMailNorrin Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.67 Safari/537.36 Edg/87.0.664.55”. Without Googling this already looks suspicious, because for the Google Chrome and Edge user agent string to show up, that says “Chromium-based Edge” to me, which wasn’t released in 2016. Looking up some further information on the user agent string, we can see that this version of Edge was released December 3 2020 and we can see an almost identical user agent string here.
Which means, no I don’t think the email is legitimate.
Question 2
The next question was a bit of a change of pace; as in, (1)0 to 100.

We already think that the email is fraudulent, and we know that since the file is an EML file then everything inside it can be modified, especially easily identified timestamps.
If we look at every timestamp, we can see a variety of standard dates, as well as unix timestamps. Decoding them all is pretty much the same timestamp, and is also wrong. So I got the first attempt wrong, thankfully there was two attempts before I couldn’t get the 100 points.
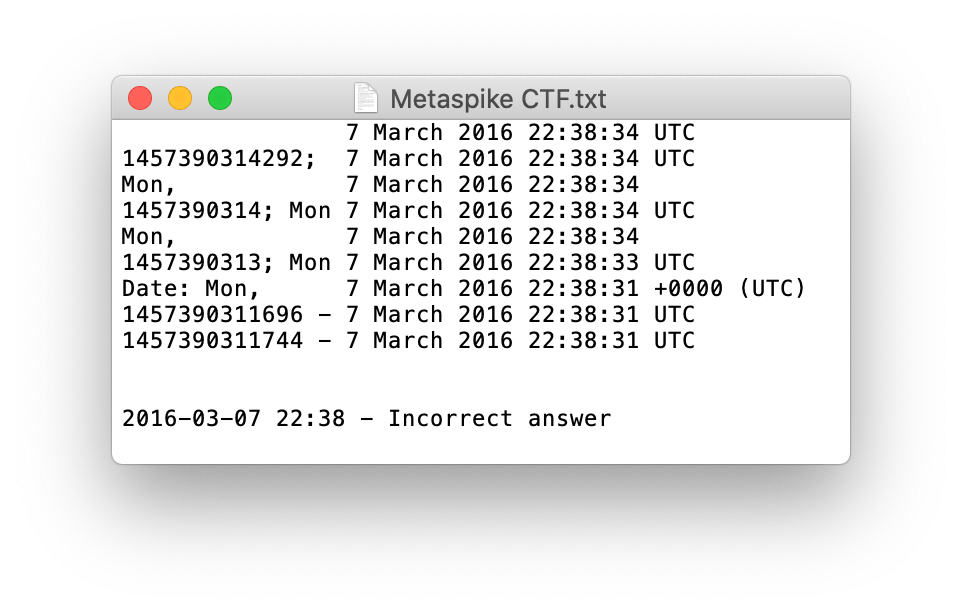
I didn’t see any other timestamps in there that might be encoded, so let’s look elsewhere.
EXIF data showed timestamps in early 2016, but that doesn’t really help us. We already have a suspicion that the email was sent in 2020, so if the attachment was created after the dates within the email that would stand out more.

Opening the file (with Adobe Reader) shows us something more interesting. It seems there’s a timestamp associated with the comment!

We don’t get the seconds, but thankfully we don’t need them for the answer! This would mean that the earliest time the email could have been sent was after the timestamp on the comment. That being said, everyone in the email could be manipulated, so technically even this timestamp could have been modified and the PDF reattached. If there was a digital signature that meant that after signing the timestamp couldn’t be modified then that would be more categorical, but we’re working with what we’ve got.
Overall, this was a very interesting challenge, and I’m very much looking forward to the rest of the CTF.
Onto challenge 2

[…] ThinkDFIRMetaspike CTF – Week 1 – “It’s legit, honest!” […]
LikeLike
[…] theme of the challenge. A bit of googling later leads me to a great writeup by Phill Moore over at thinkdfir.com. His conclusion was based on an X-Mailer string anomaly. The X-mailer field shows the software used […]
LikeLike