There’s a new (newish?) database in Microsoft Edge that is worth exploring a bit further. This blogpost is partially an intro, partially a placeholder, because I saw some conversation on a listserv about the database but almost nothing else online about it. There’s limited research, so let me know what you find and I can update the post!
Read More »Category: Uncategorized
CPY JMP
I’m teaching FOR500 Windows Forensic Analysis in Singapore this week and something that was recently added to the class relates to a new(ish) discovery into the operation of Jumplists on Windows 10.
During an update to the class it was discovered that when a folder is copied, the AutomaticDestination Jumplist file associated with Windows Explorer will track the folder copy operation as an interaction. How cool! Unfortunately this only relates to folder copies and not file copies but I’ll take it.
Read More »Timestamps in INDX Entries
Welcome to 2023!
Turns out I didn’t post on here as much as I should have last year. Logging in this morning I can see I posted twice, whoops. Let’s change that with some validation research into INDX records, particularly in relation to the timestamps that are stored in INDX entries.
I’ve been putting together my talk for the upcoming Magnet Virtual Summit, and my talk is about carving out forensic artefacts from an encrypted VHDX file that I had during an ransomware investigation last year. During my investigation I had to use a variety of tools to piece together a timeline of activity from a blob of partially encrypted data, which was an interesting process.
One of the artefacts that I used was INDX records, which has lead me to play with a number of different tools and processes. The point of this post relates to the timestamps that you can find when parsing $I30 entries.
Read More »Tracking screenshots with LNK files
At some point in history, Microsoft introduced Snipping Tool. The world rejoiced as a simple screenshot tool was added to Windows that allowed for screenshots of sections of the screen that was easier than pressing Print-Screen and opening Paint.
Unfortunately, Microsoft decided to deprecate Snipping tool in later versions of Win10, instead pushing people onto the (in my opinion) less user friendly “Snip-n-Sketch”. However, not all is lost with the change, and in fact, forensic artefacts are gained!
I tried to think of a pun for a title, I was unsuccessful. Insert semi relevant picture!

Snipping Tool
I took a screenshot with ‘Snipping tool’ and that didn’t create a LNK file. The contents of the screenshot were put in the clipboard, which is the default setting (so if clipboard sync was on it would likely be written to disk and stored in memory).
After the screenshot is taken it opens a new window showing the picture, and when the screenshot is saved, a new file is created and the forensic artifacts associated should be populated. From a LNK perspective, there will be a new LNK file created with its parent folder and the MAC times for both the LNK and the Target should match.
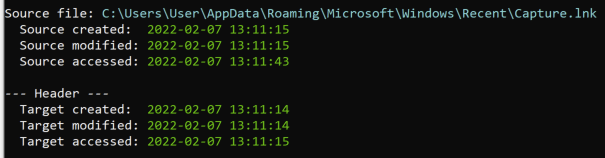
‘Snip & Sketch’
‘Snip & Sketch’ is its own application, and it also has a shortcut key (Win+Shift+S). Interestingly, taking a screenshot with the shortcut key results in a notification being displayed in the bottom right but no automatically created LNK files. If the user was to click on the notification that is displayed, then the picture will open in ‘Snip & Sketch’, which generates a LNK file indicating the source is ‘Toast’ (as in notification).
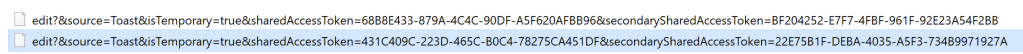
More interestingly, taking a screenshot through the application results in a LNK file without interaction!
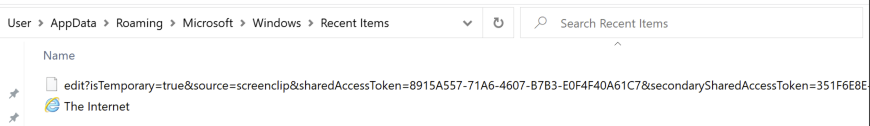
If you go through the app to the point of taking a screenshot, but then don’t follow through, you will still get a LNK file but it won’t have the GUIDs.
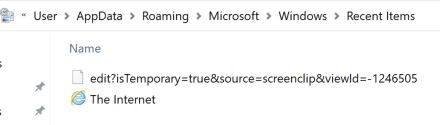
Overall, it seems that the ‘Snip & Sketch’ app is what generates the LNK file.
What was the screenshot though?
As an addendum – ‘Snip & Sketch’ is a Windows app, and so I had a look in the Appdata\Local\Packages folder:
C:\Users\User\AppData\Local\Packages\Microsoft.ScreenSketch_8wekyb3d8bbwe
While there are a few folders in here, the main one that has content is the TempState folder. What was crazy was this contained the screenshots that I took but never saved to disk.
I have no idea why this is here or how long these files are retained for – they survive a restart, so there’s probably some arbitrary process that clears them out.
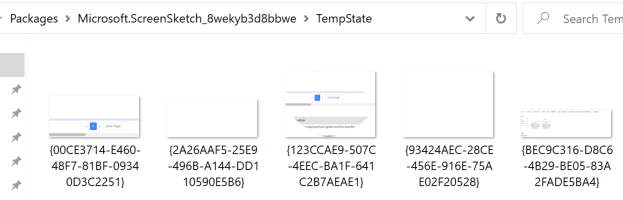
Some research online suggests that some additional screenshots may exist in a seperate location, however I couldn’t recreate what were in the posts.
There’s a lot of intricacies left to learn in the Windows operating system – nothing is a solved problem!
References:
Snip & Sketch Autosave Location – https://www.reddit.com/r/Windows10/comments/iv8gf8/snip_sketch_autosave_location/
I can see and hear you seeing and hearing me!
In preparation for an upcoming FOR500 class I thought I would test out one of the recent additions to the class. This post by my colleague Zach shows that Win10 1903 and later has a registry key that will store the full path of any executable that utilises the computers camera or microphone.
Read More »Introducing Awesome BEC
Business email compromise is anything but awesome. According to the FBI, in 2020 cybercriminals cost US companies 2 billion through exploitation of business email systems.
I started an Awesome list to try and compile all of the links that I had previously just kept in my head for reference when doing a BEC investigation. It’s still very much a work in progress, and I hope people a) find it useful and b) contribute to it to make it even better.
You can see the nice looking version here, and if you’d like to contribute please send pull requests and issues here.
I haven’t had a chance to add summaries/descriptions of the links referenced, and I’m considering adding a couple of other sections related to hunting for phishing emails (typically how a BEC has occurred in my experience) as well as email header analysis.
Keen for contributions and hope it helps people!
You want me to deal with how many VMDKs!?
Recently I was given approximately 55 VMDKs after a cyber incident to try and identify the root cause. Ideally, these systems would be online so that we could deploy our distributed threat hunting and forensic analysis tool of choice, Velociraptor however this wasn’t a possibility in this scenario.
This means I had an interesting problem to solve; how do I get the relevant forensic artefacts that I wanted to so that I could triage the VMDKs and identify which systems that I wanted to dig deeper into.
Read More »Metaspike CTF – Week 6 – “HODL onto your timestamps”
Over the halfway point! (I appreciate week 6 was a while ago, I haven’t had a chance to clean up my write up for this until now). This week we’re looking at email authentication again, trying to identify the actual date of an email. I scraped this one by with only hours to spare, and chatting with the others it was interesting to see the different approaches taken.
Read More »Metaspike CTF – Week 5 – “Spot the DFIRence”
I write my notes as I go along, but sometimes it takes me a bit to get it into a blogable format. This week took a little longer because I had to wait for Armans walkthrough. I got super close to the answer for part 3, but unfortunately missed out on the 100 points.
We’re back looking at EML files to help assist validating a story and identifying forgery, and get to play with an interesting technique!
Read More »Metaspike CTF – Week 4 – “IM APparently making this harder than it was meant to be”
Starting this post by admitting it took me a lot longer to get the answers to some of these questions than it should have, because I misunderstood some of the wording of the questions. I ended up going down a lot of RFC-related rabbitholes, only to find that certain parts were theoretical and others practical. Well, we all make mistakes, onto the post!
Read More »