In preparation for an upcoming FOR500 class I thought I would test out one of the recent additions to the class. This post by my colleague Zach shows that Win10 1903 and later has a registry key that will store the full path of any executable that utilises the computers camera or microphone.
Zach shows that this is stored in the following key
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\CapabilityAccessManager
During my testing I found, at least on Win10 20H2, that the data may also be stored in the same location but under the current user (HKCU/HKU –> NTUSER.DAT). This possibly has something to do with the way the executable is stored/installed/executed.
I replicated Zach’s research by generating a Msfvenom payload, following the steps here and then manually launched the Meterpreter reverse shell under the user profile (not as admin). This allowed me to utilise the various functions in Metasploit to turn on my victim VM’s webcam (which was a bit fiddly in VMware because I had to make sure I added it to my VM, same with the sound card) and also used my victim VM’s microphone to record a short audio clip.
Insert grainy picture!
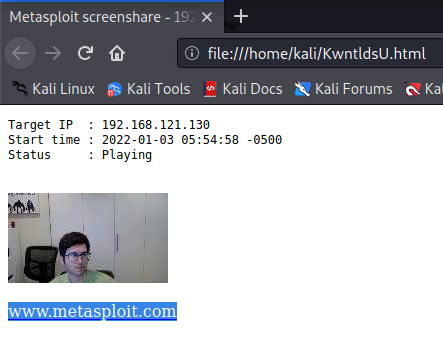
After doing so I grabbed a triage collection with KAPE and then did some registry searches for my executable name
As shown in the screenshot below, the full path of my executable was listed within the affected users NTUSER rather than HKLM (SOFTWARE hive).
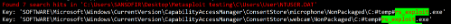
Checking the same key on my regular computer shows things like zoom and steam; apps I would expect to see here. I did also notice rundll in there (which is probably fine maybe? on an investigation I’d look into it more). If someone was to execute their malware with rundll rather than a regular executable that’s probably what you would see (which no clues as to what the malicious payload actually was).
So my regular computer had populated keys under HKU/HKCU and HKLM. Good to know!
Additional testing required
If someone wants to expand on this the questions that would be good to have answered are:
- If you run a malicious DLL with rundll or any other lolbin would this then be recorded as we expect with the full path of the lolbin?
- Is there a way to identify why something has been recorded in the SOFTWARE hive compared to the USER hive. OR, did Microsoft change the location between versions and therefore the stuff in my SOFTWARE hive is just a remnant from an upgrade?
- Are there any other indicators that can be used to identify if and when a malicious attacker had turned on the microphone or webcam!?
- This one I’m thinking less about the Meterpreter/Cobalt Strike OST side of things and more along the lines of any of the ‘banking trojans’ that may have modules for listening and seeing.

[…] ThinkDFIRI can see and hear you seeing and hearing me! […]
LikeLike